Hgame CTF 2025题目复现
REverse
Turtle
- 用
Exeinfo PE打开发现是upx壳,而且题目也提示了需要脱壳,upx壳被魔改过了,用普通脱壳工具无效,于是手动脱壳。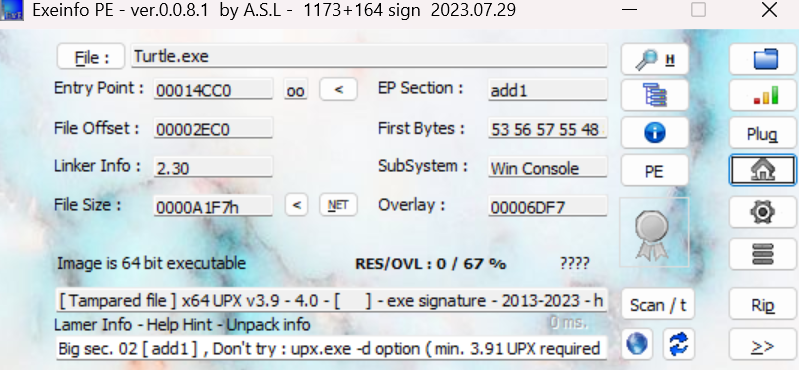
ps:有的魔改后的upx壳可以在010editor中改(把add0->upx0,add1->upx1……,本题为只读文件改不了)
- 用xdbg64打开,oep脱壳定律找到大跳转,打断点
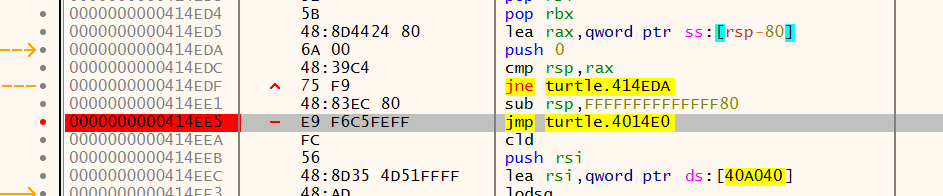
- F9运行,接着用
ScyllaDump,oep为00000000004014E0,生成Turtle_dump.exe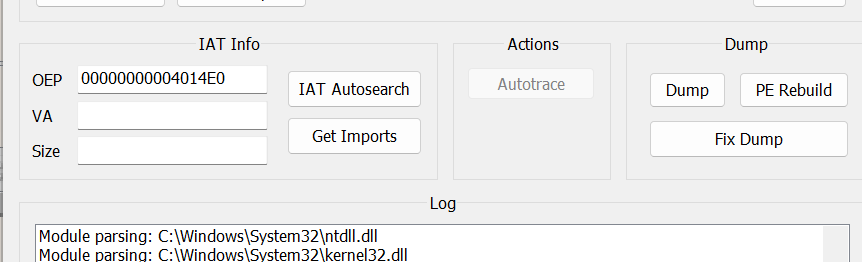
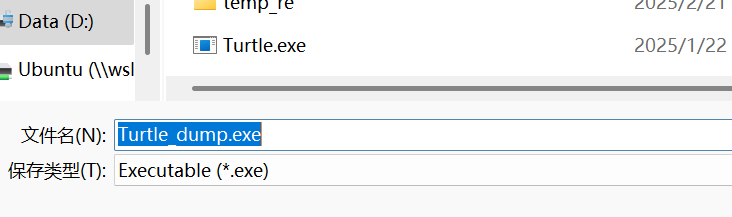
接着先后点击IAT Autosearch,Get Imports,Fix Dump,这里打开Turtle_dump.exe,之后打开文件夹就会看到新生成的Turtle_dump_SCY.exe文件了。
- 将Turtle_dump_SCY.exe用IDA(64)打开,发现可以正常地看到函数了,找到main函数,F5反汇编一下
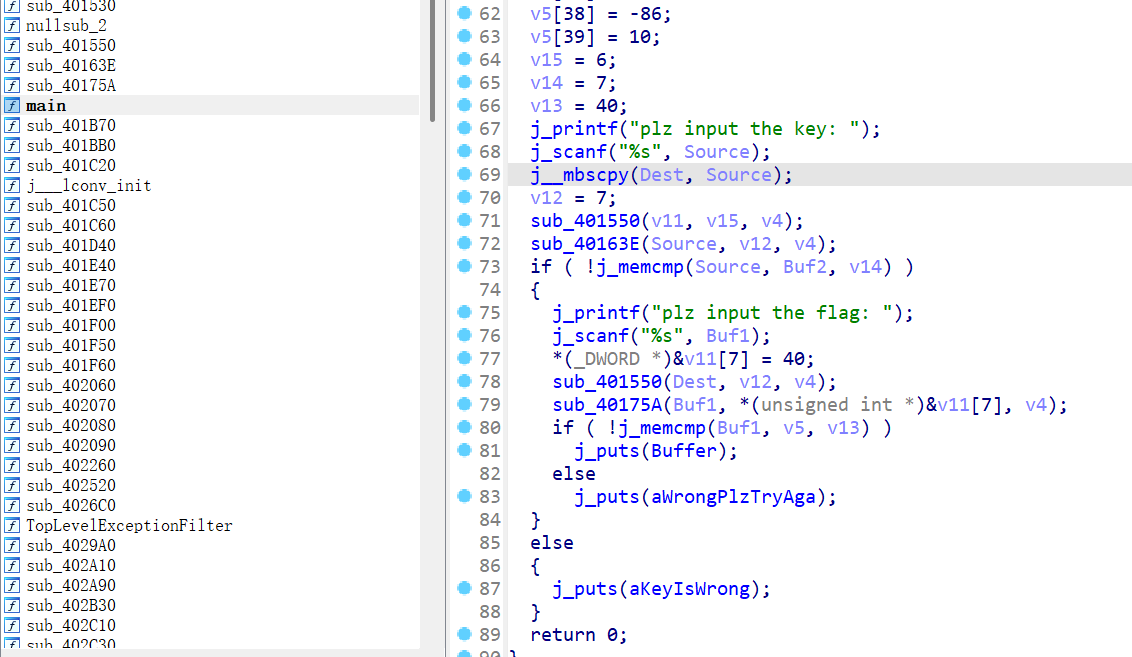
- 点开函数后可以看出sub_401550是rc4 init,而sub_40163E(标准)和sub_40175A(魔改)是两个rc4
- 解出flag
1 | |
flag: hgame{Y0u’r3_re4l1y_g3t_0Ut_of_th3_upX!}
尊嘟假嘟
- 在 MuMu模拟器 打开 apk,点击下方 尊嘟 假嘟 按钮的话就是让图片跳转,但其实你分别在两个界面点图片的能发现出现了”0.o”和”o.0” 的字符,并且是逐渐加长的
- 用 jadx 打开 apk,先看到有一个
DexCall类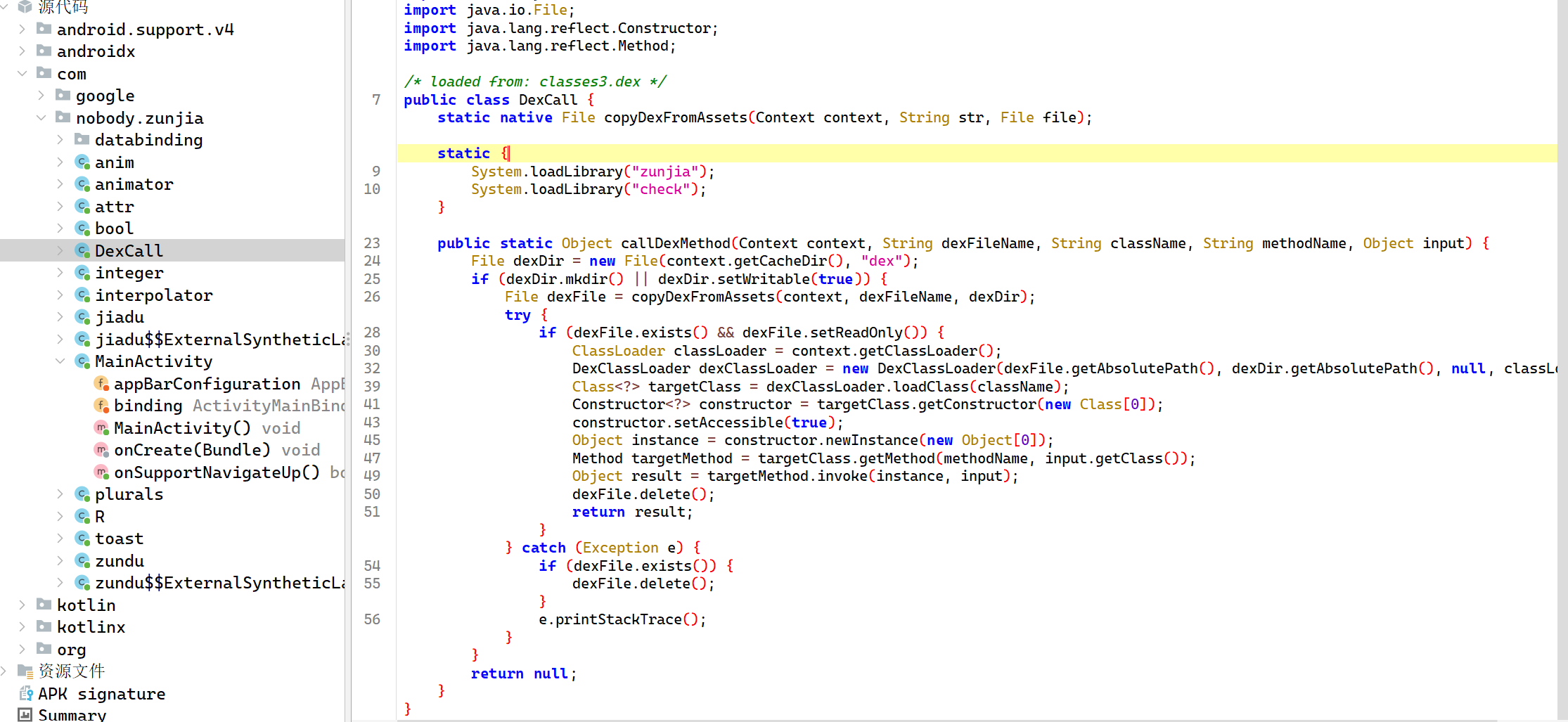
静态加载了两个本地库“zunjia”和“check”,注意到核心方法callDexMethod,动态加载.dex文件
1 | |
最后又将 dex 文件删掉,这让我想到之前做的一道 Find My Dex 的题目,于是准备先用 frida hook 拿出这个被删掉的 dex 文件
frida-server连一下
hook 出 dex 文件的地址
1 | |
注意这里需要点击图片才能触发DexCall.callDexMethod,点callDexMethod x 交叉引用跳转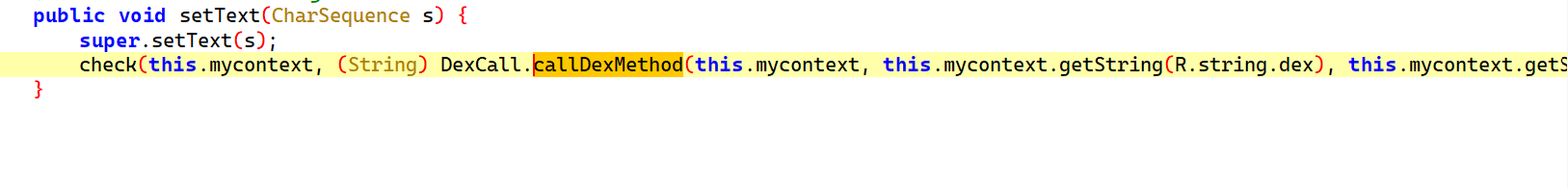
点setText x 交叉引用跳转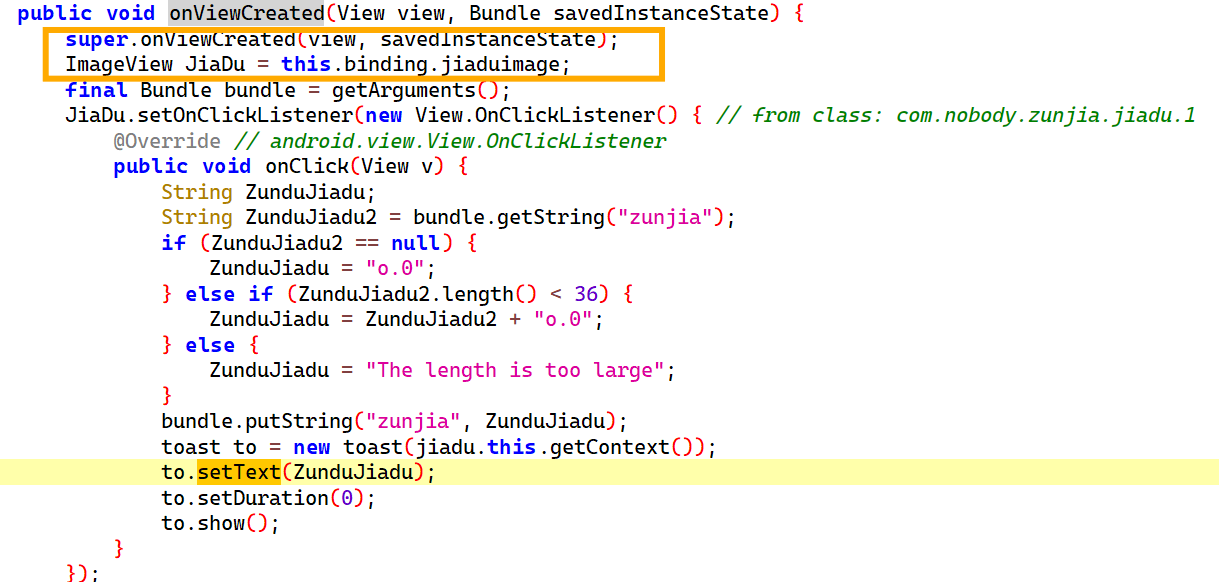
而这个 JiaDu 是 ImageView
触发后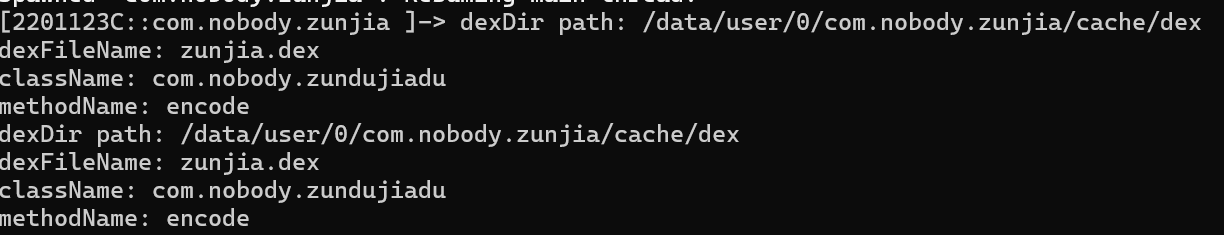
可以知道这个 dex 文件的地址是在/data/user/0/com.nobody.zunjia/cache/dex
再用一个脚本把它hook出来
1 | |
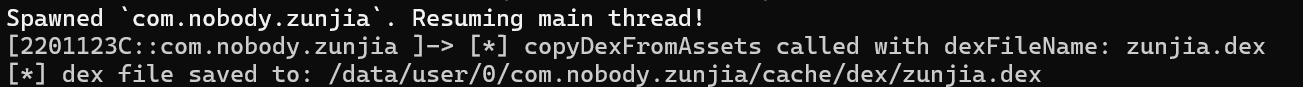
这个路径下没有权限不能直接进行提取,先把它转移到另外的文件夹,再用 adb pull 提取出来
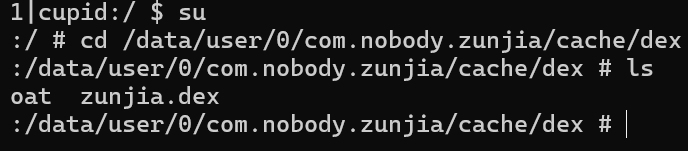
可以看到这个路径下多了一个zunjia.dex文件,然后执行
1 | |
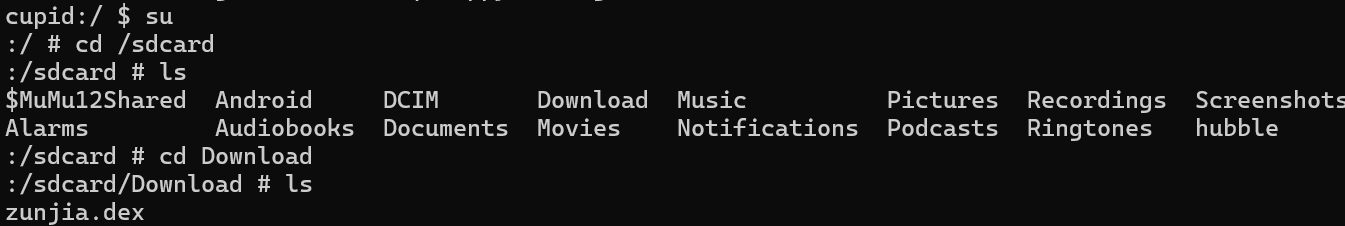
1 | |
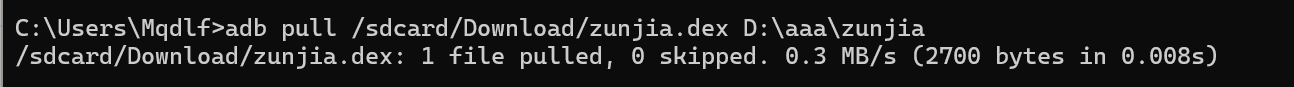
这样就把 dex 文件提取到本地了,然后在 jadx 中把这个文件也添加进去,可以看到多了的内容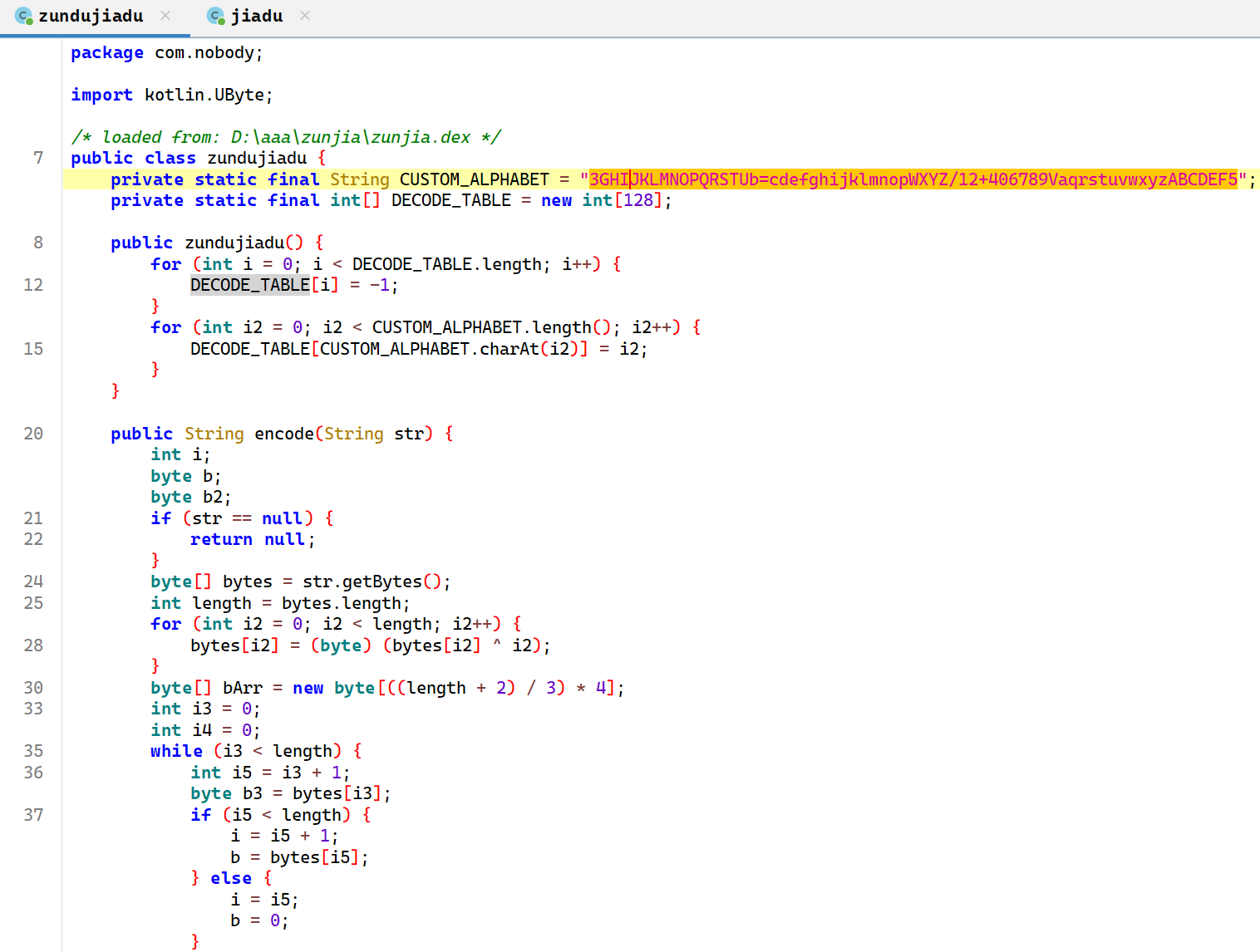
base64换表
有个 toast 类,里面有一个 native 的check 函数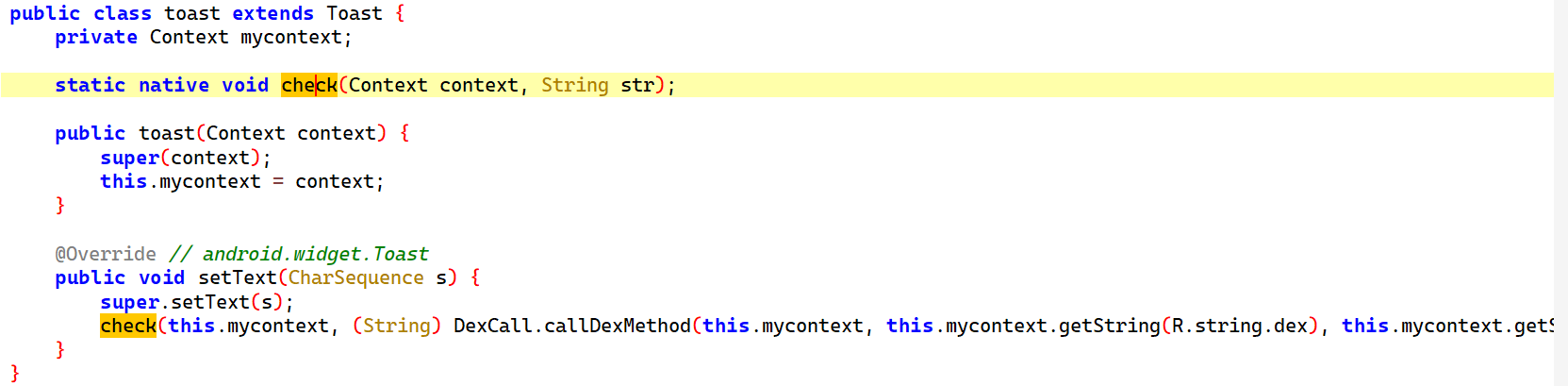
1 | |
在resources.arsc的 res/values/strings.xml 中可以看到对应的字符串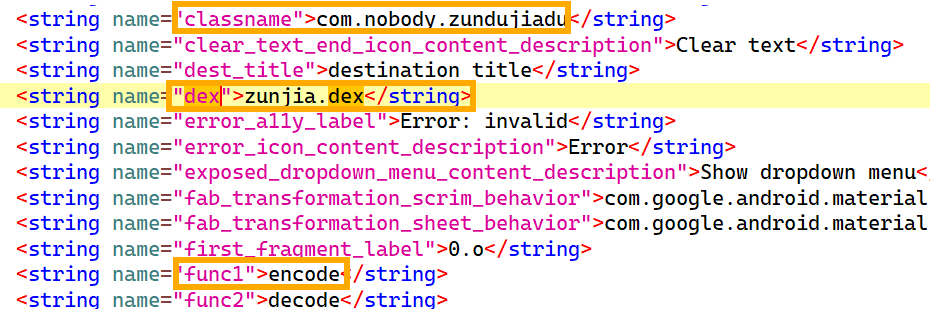
所以这个其实是
1 | |
分析 check.so 文件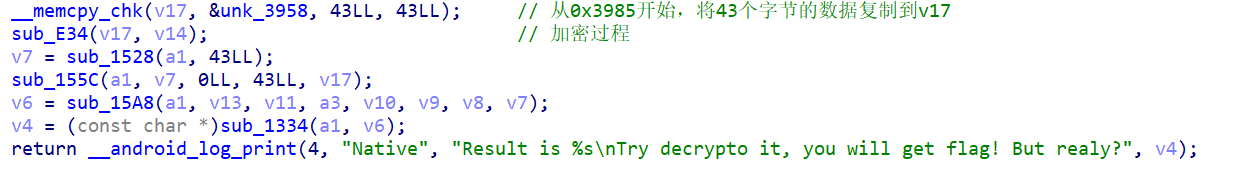
获取密文数据,ida 脚本
1 | |
加密函数点进去看是rc4
1 | |
b’hgame{4af153b9-ed3e-420b-978c-eeff72318b49}’
Hgame CTF 2025题目复现
http://example.com/2025/02/23/2/