你是真的大学生吗? 附件是MS-DOS executable (EXE)文件,ida 不能反编译,硬看汇编
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 ''' T[20]=C[20]^C[0] al=T[20] T[19]=C[19]^al即T[19]=C[19]^T[20] al=T[19] T[18]=C[18]^al即T[18]=C[18]^T[19] ... T[0]=C[0]^al即T[0]=C[0]^T[1] 所以对于i=0~19 T[i]=C[i]^T[i+1] 求C[i]就用C[i]=T[i]^T[i+1] 对于i=20 C[20]=T[20]^C[0] C[20]=T[20]^(T[0]^T[1]) ''' 0x76 , 0x0E , 0x77 , 0x14 , 0x60 , 0x06 , 0x7D , 0x04 , 0x6B , 0x1E , 0x41 , 0x2A , 0x44 , 0x2B , 0x5C , 0x03 , 0x3B , 0x0B , 0x33 , 0x05 ]for i in range (len (enc)-1 ):1 ])1 ]^enc[0 ]^enc[1 ])print ('' .join([chr (c) for c in flag]))
flag 为yctf{you_know_8086}
给阿姨倒一杯卡布奇诺 经典的 TEA 了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 #include <stdio.h> #define uint32_t unsigned int void decrypt (uint32_t *v, uint32_t *key) static uint32_t data1 = 0x5F797274 ;static uint32_t data2 = 0x64726168 ;int i; uint32_t sum; uint32_t v1; uint32_t v0; 0x6E75316C * 32 ;uint32_t data1_tmp = v[0 ];uint32_t data2_tmp = v[1 ];0 ];1 ];for (i = 31 ; i >= 0 ; i--)5 ) + key[3 ]) ^ (v0 + sum) ^ (key[2 ] + 16 * v0) ^ (sum + i);5 ) + key[1 ]) ^ (v1 + sum) ^ (key[0 ] + 16 * v1) ^ (sum + i);0x6E75316C ;0 ] = v0 ^ data1;1 ] = v1 ^ data2;int main () uint32_t key[4 ]; uint32_t array[8 ]; 0 ] = 0x9B28ED45 ;1 ] = 0x145EC6E9 ;2 ] = 0x5B27A6C3 ;3 ] = 0xE59E75D5 ;4 ] = 0xE82C2500 ;5 ] = 0xA4211D92 ;6 ] = 0xCD8A4B62 ;7 ] = 0xA668F440 ;0 ] = 0x65766967 ;1 ] = 0x756F795F ;2 ] = 0x7075635F ; 3 ] = 0x6165745F ;for (int i = 0 ; i <= 7 ; i += 2 )decrypt (array + i, key);for (int i=0 ; i<32 ; i++)printf ("%c" , ((char *)array)[i]);return 0 ;
flag 为XTCTF{133bffe401d223a02385d90c5f1ca377}
DebugMe jadx 打开有混淆,用 jeb 打开能正常反编译,安卓 java 层动调,Frida 一把梭,hook What类
1 2 3 4 5 6 7 8 9 10 11 12 13 function hookwhat (var what = Java .use ("com.xyctf.ezapk.What" );var enc = "WikFhRxyYjoSJ8mMbM3fRwty/74bc7Ip7ojqenHaSqc9wDv3JDG9XfV6xEiC7Eg1RWTUa4LaM%2BD0W%2BPKanSA5w==" ;var flag = what.x (enc);console .log ("\nFlag: " + flag);function main (Java .perform (function (hookwhat ();setImmediate (main);
直接出 flagXYCTF{d3bugg3r_15_v3ry_u53ful}
何须相思煮余年 附件是 txt,将 16 进制数据放进 CyberChef 里,选择From Hex,然后在 Output 保存文件
1 2 3 push ebp ; 保存旧的栈基址sub esp , 0x20
1 2 3 leave mov esp , ebp ret
按 P 创建函数后 F5能反编译了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 enc=[88 ,88 ,134 ,87 ,74 ,118 ,318 ,101 ,59 ,92 ,480 ,60 ,65 ,41 ,770 ,110 ,73 ,31 ,918 ,39 ,120 ,27 ,1188 ,47 ,77 ,24 ,1352 ,44 ,81 ,23 ,1680 ,46 ,85 ,15 ,1870 ,66 ,91 ,16 ,4750 ]for i in range (len (enc)):if i%4 ==0 :elif i%4 ==1 :elif i%4 ==2 :if i!=0 :elif i%4 ==3 :print ('' .join([chr (c) for c in result]))
flag 为XYCTF{5b3e07567a9034d06851475481507a75}
what’s this 用 exeinfope打开看发现 Lua bytecode (generic),用 luadec 反编译
1 2 3 4 5 6 7 8 9 10 import base64"==AeuFEcwxGPuJ0PBNzbC16ctFnPB5DPzI0bwx6bu9GQ2F1XOR1U" "6" ,"W" )1 ]for i in dec.decode():ord (i)-3 )^8 print (chr (i),end="" )
flag 为XYCTF{5dcbaed781363fbfb7d8647c1aee6c}
ez_enc main 函数中加密,byte_14001E008 里是密文,z3求解
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 from z3 import *0x27 , 0x24 , 0x17 , 0x0B , 0x50 , 0x03 , 0xC8 , 0x0C , 0x1F , 0x17 , 0x36 , 0x55 , 0xCB , 0x2D , 0xE9 , 0x32 , 0x0E , 0x11 , 0x26 , 0x02 , 0x0C , 0x07 , 0xFC , 0x27 , 0x3D , 0x2D , 0xED , 0x35 , 0x59 , 0xEB , 0x3C , 0x3E , 0xE4 , 0x7D ]'flag[%d]' %i,8 ) for i in range (34 )]for i in range (34 ):127 )31 )for i in range (33 ):b'IMouto' [i%6 ]^(item[i+1 ]+item[i]%20 )&0xff for i in range (34 ):if s.check()==sat:print ('' .join(chr (m[dec[i]].as_long()) for i in range (34 )))
flag 为flag{!_r3ea11y_w4nt_@_cu7e_s1$ter}
ezmath python 逆向,先用 pyinstxtractor 解包,找到ezmath.pyc,用 https://tool.lu/pyc 反编译得到代码
1 2 3 4 5 6 7 lambda .0 : [ ord (i) for i in .0 ])(input ('flag:' ))if len (flag) == 32 and (((((((((((((((((((((sum ((lambda .0 : [ flag[23 ] for _ in .0 ])(range (flag[23 ]))) + sum ((lambda .0 : [ flag[12 ] for _ in .0 ])(range (flag[12 ]))) + sum ((lambda .0 : [ flag[1 ] for _ in .0 ])(range (flag[1 ]))) - sum ((lambda .0 : [ flag[24 ] for _ in .0 ])(range (222 )))) + sum ((lambda .0 : [ flag[22 ] for _ in .0 ])(range (flag[22 ]))) + sum ((lambda .0 : [ flag[31 ] for _ in .0 ])(range (flag[31 ]))) + sum ((lambda .0 : [ flag[26 ] for _ in .0 ])(range (flag[26 ]))) - sum ((lambda .0 : [ flag[9 ] for _ in .0 ])(range (178 ))) - sum ((lambda .0 : [ flag[29 ] for _ in .0 ])(range (232 )))) + sum ((lambda .0 : [ flag[17 ] for _ in .0 ])(range (flag[17 ]))) - sum ((lambda .0 : [ flag[23 ] for _ in .0 ])(range (150 ))) - sum ((lambda .0 : [ flag[6 ] for _ in .0 ])(range (226 ))) - sum ((lambda .0 : [ flag[7 ] for _ in .0 ])(range (110 )))) + sum ((lambda .0 : [ flag[19 ] for _ in .0 ])(range (flag[19 ]))) + sum ((lambda .0 : [ flag[2 ] for _ in .0 ])(range (flag[2 ]))) - sum ((lambda .0 : [ flag[0 ] for _ in .0 ])(range (176 )))) + sum ((lambda .0 : [ flag[10 ] for _ in .0 ])(range (flag[10 ]))) - sum ((lambda .0 : [ flag[12 ] for _ in .0 ])(range (198 )))) + sum ((lambda .0 : [ flag[24 ] for _ in .0 ])(range (flag[24 ]))) + sum ((lambda .0 : [ flag[9 ] for _ in .0 ])(range (flag[9 ]))) - sum ((lambda .0 : [ flag[3 ] for _ in .0 ])(range (168 )))) + sum ((lambda .0 : [ flag[8 ] for _ in .0 ])(range (flag[8 ]))) - sum ((lambda .0 : [ flag[2 ] for _ in .0 ])(range (134 )))) + sum ((lambda .0 : [ flag[14 ] for _ in .0 ])(range (flag[14 ]))) - sum ((lambda .0 : [ flag[13 ] for _ in .0 ])(range (170 )))) + sum ((lambda .0 : [ flag[4 ] for _ in .0 ])(range (flag[4 ]))) - sum ((lambda .0 : [ flag[10 ] for _ in .0 ])(range (142 )))) + sum ((lambda .0 : [ flag[27 ] for _ in .0 ])(range (flag[27 ]))) + sum ((lambda .0 : [ flag[15 ] for _ in .0 ])(range (flag[15 ]))) - sum ((lambda .0 : [ flag[15 ] for _ in .0 ])(range (224 )))) + sum ((lambda .0 : [ flag[16 ] for _ in .0 ])(range (flag[16 ]))) - sum ((lambda .0 : [ flag[11 ] for _ in .0 ])(range (230 ))) - sum ((lambda .0 : [ flag[1 ] for _ in .0 ])(range (178 )))) + sum ((lambda .0 : [ flag[28 ] for _ in .0 ])(range (flag[28 ]))) - sum ((lambda .0 : [ flag[5 ] for _ in .0 ])(range (246 ))) - sum ((lambda .0 : [ flag[17 ] for _ in .0 ])(range (168 )))) + sum ((lambda .0 : [ flag[30 ] for _ in .0 ])(range (flag[30 ]))) - sum ((lambda .0 : [ flag[21 ] for _ in .0 ])(range (220 ))) - sum ((lambda .0 : [ flag[22 ] for _ in .0 ])(range (212 ))) - sum ((lambda .0 : [ flag[16 ] for _ in .0 ])(range (232 )))) + sum ((lambda .0 : [ flag[25 ] for _ in .0 ])(range (flag[25 ]))) - sum ((lambda .0 : [ flag[4 ] for _ in .0 ])(range (140 ))) - sum ((lambda .0 : [ flag[31 ] for _ in .0 ])(range (250 ))) - sum ((lambda .0 : [ flag[28 ] for _ in .0 ])(range (150 )))) + sum ((lambda .0 : [ flag[11 ] for _ in .0 ])(range (flag[11 ]))) + sum ((lambda .0 : [ flag[13 ] for _ in .0 ])(range (flag[13 ]))) - sum ((lambda .0 : [ flag[14 ] for _ in .0 ])(range (234 )))) + sum ((lambda .0 : [ flag[7 ] for _ in .0 ])(range (flag[7 ]))) - sum ((lambda .0 : [ flag[8 ] for _ in .0 ])(range (174 )))) + sum ((lambda .0 : [ flag[3 ] for _ in .0 ])(range (flag[3 ]))) - sum ((lambda .0 : [ flag[25 ] for _ in .0 ])(range (242 )))) + sum ((lambda .0 : [ flag[29 ] for _ in .0 ])(range (flag[29 ]))) + sum ((lambda .0 : [ flag[5 ] for _ in .0 ])(range (flag[5 ]))) - sum ((lambda .0 : [ flag[30 ] for _ in .0 ])(range (142 ))) - sum ((lambda .0 : [ flag[26 ] for _ in .0 ])(range (170 ))) - sum ((lambda .0 : [ flag[19 ] for _ in .0 ])(range (176 )))) + sum ((lambda .0 : [ flag[0 ] for _ in .0 ])(range (flag[0 ]))) - sum ((lambda .0 : [ flag[27 ] for _ in .0 ])(range (168 )))) + sum ((lambda .0 : [ flag[20 ] for _ in .0 ])(range (flag[20 ]))) - sum ((lambda .0 : [ flag[20 ] for _ in .0 ])(range (212 )))) + sum ((lambda .0 : [ flag[21 ] for _ in .0 ])(range (flag[21 ]))) + sum ((lambda .0 : [ flag[6 ] for _ in .0 ])(range (flag[6 ]))) + sum ((lambda .0 : [ flag[18 ] for _ in .0 ])(range (flag[18 ]))) - sum ((lambda .0 : [ flag[18 ] for _ in .0 ])(range (178 )))) + 297412 == 0 :print ('yes' )
分析一下主要表达式sum((lambda .0: [ <参数1> for _ in .0 ])(range(<参数2>)))lambda .0: [ <参数1> for _ in .0 ] 定义了一个匿名函数,接受参数.0(即range(<参数2>)生成的序列)range(<参数2>) 生成一个长度为<参数2>的整数序列(如<参数2>=3时生成0,1,2)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from z3 import *f'flag{i} ' ) for i in range (32 )]23 ] ** 2 ) + (flags[12 ] ** 2 ) + (flags[1 ] ** 2 ) - (222 * flags[24 ]) + (flags[22 ] ** 2 ) +31 ] ** 2 ) + (flags[26 ] ** 2 ) - (178 * flags[9 ]) - (232 * flags[29 ]) + (flags[17 ] ** 2 ) -150 * flags[23 ]) - (226 * flags[6 ]) - (110 * flags[7 ]) + (flags[19 ] ** 2 ) + (flags[2 ] ** 2 ) -176 * flags[0 ]) + (flags[10 ] ** 2 ) - (198 * flags[12 ]) + (flags[24 ] ** 2 ) + (flags[9 ] ** 2 ) -168 * flags[3 ]) + (flags[8 ] ** 2 ) - (134 * flags[2 ]) + (flags[14 ] ** 2 ) - (170 * flags[13 ]) +4 ] ** 2 ) - (142 * flags[10 ]) + (flags[27 ] ** 2 ) + (flags[15 ] ** 2 ) - (224 * flags[15 ]) +16 ] ** 2 ) - (230 * flags[11 ]) - (178 * flags[1 ]) + (flags[28 ] ** 2 ) - (246 * flags[5 ]) -168 * flags[17 ]) + (flags[30 ] ** 2 ) - (220 * flags[21 ]) - (212 * flags[22 ]) - (232 * flags[16 ]) +25 ] ** 2 ) - (140 * flags[4 ]) - (250 * flags[31 ]) - (150 * flags[28 ]) + (flags[11 ] ** 2 ) +13 ] ** 2 ) - (234 * flags[14 ]) + (flags[7 ] ** 2 ) - (174 * flags[8 ]) + (flags[3 ] ** 2 ) -242 * flags[25 ]) + (flags[29 ] ** 2 ) + (flags[5 ] ** 2 ) - (142 * flags[30 ]) - (170 * flags[26 ]) -176 * flags[19 ]) + (flags[0 ] ** 2 ) - (168 * flags[27 ]) + (flags[20 ] ** 2 ) - (212 * flags[20 ]) +21 ] ** 2 ) + (flags[6 ] ** 2 ) + (flags[18 ] ** 2 ) - (178 * flags[18 ]) + 297412 == 0 if solver.check() == sat:str (model[flag]) if model[flag] is not None else '0' for flag in flags]print (' ' .join(result))else :print ("No solution found." )
这个好像要把类型设置成Real 才跑得出来,用 Int 类型没解出来XYCTF{q7WYGscUuptTYXjnjKoyUTKtG}
Trustme jadx 打开,在 MainAcitity 里看到标准RC4,并且给出了密文和密钥
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 def rc4_dec (ciphertext, key ):list (range (256 ))0 for i in range (256 ):len (key)]) % 256 0 for byte in ciphertext:1 ) % 256 256 256 ]return bytes (plaintext)0x5A ,0X3C ,0X46 ,0XE0 ,0X22 ,0X8B ,0X44 ,0X4D ,0XEC ,0XC7 ,0X65 ,0X1C ,0X8A ,0X7C ,0XA9 ,0X3B ,0XA4 ,0XCB ,0X35 ,0XA4 ,0X6F ,0X7E ,0XB5 ,0X89 ,0XBE ,0XF4 ]b'XYCTF' print (dec_data.decode('utf-8' ))
输出为 The Real username is adminadmin' --,密码随意SELECT * FROM users WHERE username = 'admin' -- ' AND password = 'anything';XYCTF{And0r1d_15_V3ryEasy}
今夕是何年 题目说的运行就能出 flag,但是在 win 和 linux 上都运行不了,用 DIE查看文件信息XYCTF{7e5165f1-385d-4fe9-1f2664d833a648a4}
easy language 三分逆向七分猜,ida 查找字符串,看到 AES-ECB XYCTF{y0u_@r3_v3ry_g00d_a7_E_l@ngu@ge}
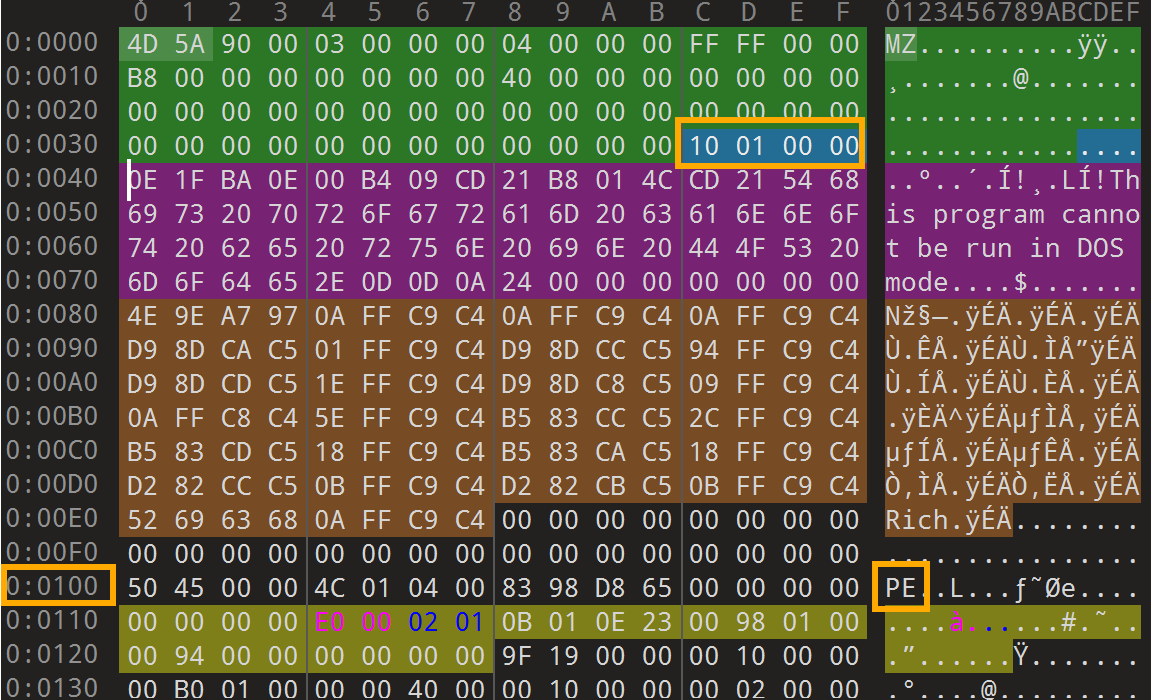
舔狗四部曲–相逢已是上上签 直接用 ida 打开看又是一坨,题目提示 PE,用 010Editor 打开10 01 00 00改成00 01 00 00,保存,把改后的 exe 再扔进 DIE 看都能发现一切正常了
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from z3 import *f'key{i} ' ) for i in range (6 )]532 * keys[5 ]+ 829 * keys[4 ]+ 258 *keys[3 ]+ 811 * keys[2 ]+ 997 * keys[1 ] + 593 * keys[0 ]== 292512 )576 *keys[5 ]+ 695 * keys[4 ]+ 602 *keys[3 ]+ 328 * keys[2 ]+ 686 * keys[1 ] + 605 * keys[0 ]== 254496 )580 *keys[5 ]+ 448 * keys[4 ]+ 756 *keys[3 ]+ 449 * keys[2 ]+ 512 * keys[1 ] + 373 * keys[0 ]== 222479 ) 597 *keys[5 ]+ 855 * keys[4 ]+ 971 *keys[3 ]+ 422 * keys[2 ]+ 635 * keys[1 ] + 560 * keys[0 ]== 295184 )524 *keys[5 ]+ 324 * keys[4 ]+ 925 *keys[3 ]+ 388 * keys[2 ]+ 507 * keys[1 ] + 717 * keys[0 ]== 251887 )414 *keys[5 ]+ 495 * keys[4 ]+ 518 *keys[3 ]+ 884 * keys[2 ]+ 368 * keys[1 ] + 312 * keys[0 ]== 211260 )if solver.check() == sat:for k in keys]'' .join(chr (val) for val in key_values)print (f"Find key: {key} " )else :print ("No solution found." )
求解flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 #include <stdio.h> #include <stdint.h> #define DELTA 0x61C88647 #define ROUNDS 12 void decrypt (uint32_t * v, int n, uint8_t * key) uint32_t sum = 0x9E3779B9 * ROUNDS; for (int i = 0 ; i < ROUNDS; i++) {uint32_t v6 = (sum >> 2 ) & 5 ; uint32_t v9 = v[n-2 ];int idx = (v6 ^ ((n-1 ) & 5 )) % 6 ;uint32_t k = key[idx];uint32_t expr = ((v9 ^ k) + (v[0 ] ^ sum)) ^ 4 ) ^ (v[0 ] >> 3 )) + 0 ] << 2 ) ^ (v9 >> 5 )));-1 ] -= expr;for (int j = n-2 ; j >= 0 ; j--) {0 ) ? v[n-1 ] : v[j-1 ]; 5 )) % 6 ; +1 ] ^ sum)) ^ 4 ) ^ (v[j+1 ] >> 3 )) + +1 ] << 2 ) ^ (v9 >> 5 )));int main () uint32_t cipher[] = {0x66697271 , 0x896E2285 , 0xC5188C1B , 0x72BCFD03 ,0x538011CA , 0x4DA146AC , 0x86630D6B , 0xF89797F0 uint8_t key[] = {'X' , 'Y' , 'C' , 'T' , 'F' , '!' };decrypt (cipher, 8 , key);printf ("Decrypted Hex:\n" );for (int i = 0 ; i < 8 ; i++) {printf ("%08X " , cipher[i]);printf ("\n\nASCII:\n" );unsigned char * flag = (unsigned char *)cipher;for (int i = 0 ; i < 32 ; i++) {printf ("%c" , flag[i]);return 0 ;
flag 为XYCTF{XXTEA_AND_Z3_1s_S0_easy!!}